Often, people are interested for a variety of reasons to avoid the use of a commercial VPN like NordVPN. Some reasons include security, data privacy, control, and cost. Hosting your own residential VPN server at home may be the preferred or only option for some, and in their research they come across three VPN options: OpenVPN, Wireguard, and Tailscale (Wireguard but with a twist). Immediately the OpenVPN protocol is usually discarded due to its vastly inferior performance to Wireguard in throughput tests in addition to being less secure/transparent. This leaves us with Wireguard and Tailscale.
Why use Wireguard over Tailscale?
Wireguard, released in 2020, is easily the most popular and best performing VPN protocol to self-host at home, and with the advent of GL.iNet routers (based on openWRT), it has become extremely easy to setup (in a matter of minutes or less!). Wireguard is completely FREE, so that means if you are a business that wants to implement Wireguard, you will not be faced with the free tier client limitations of Tailscale. Wireguard also involves NO 3rd party unlike Tailscale which does route your traffic (albeit encrypted). The major downside of this 3rd party routing/relaying with Tailscale is that their public TCP relay servers, which are used when a direct UDP connection cannot be established, can throttle your speeds to as low as 5 Mbps up/down. More on that below...
Why use Tailscale over Wireguard?
First, to be clear, Tailscale IS Wireguard but wrapped in its own client application. Connections are still done using Wireguard, but authentications, settings, and relay server management is done using proprietary Tailscale code. That said, Tailscale has some significant advantages over bare Wireguard in specific scenarios. First, if the Wireguard server port you have chosen (default: 51820) or UDP is blocked by the firewall of the network you connect to while traveling, you will not be able to connect to your VPN. With Tailscale, it will find a way. The other scenario is if your home internet source (your ISP) at your server location uses carrier grade NAT (CGNAT), you will NOT be able to use bare Wireguard to host the VPN server (unless you use a 3rd party VPS such as Oracle cloud or another workaround). Again, this is where Tailscale comes to the rescue with its NAT hole-punching and its encrypted, public DERP relay servers. In this case, your internet traffic will be routed through one of Tailscale’s worldwide relay servers depending on proximity. The downside is that these servers are throttled since they must accommodate many other users in addition to you. Therefore, the internet speed will be significantly reduced (often <10 Mbps up/down) and latency may also increase some. Don’t worry though, your IP will still show as your home Tailscale “exit node” IP, but there is a little more uncertainty in performance. Fortunately, you can purchase a monthly subscription to have access to your own custom DERP relay server, unthrottled, on my Tiers page with the Diamond Tier.
Despite not having a direct, UDP connection in this particular scenario, at least Tailscale will still enable you to have a connection back to your home server (to simply route your internet traffic, gain access to NAS, etc.) while Wireguard would not. Another advantage of Tailscale is that it does not require us to port forward, nor do we need our own dynamic DNS service for a non-static public IP at the server location. Tailscale takes care of all of this!
](https://cdn-images-1.medium.com/max/2088/1*ubOQWcqmBXmhN4j-5Y3ZzA.png)
A data point for Wireguard vs. Tailscale internet speed performance
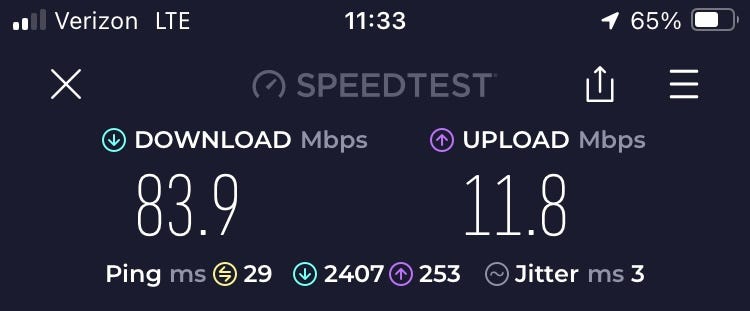
Local LTE connection (No VPN)
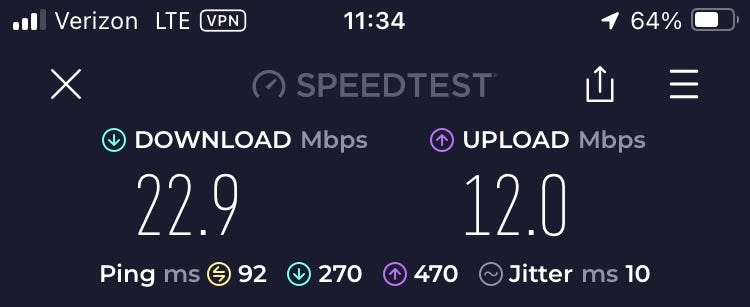
Connected to Wireguard server on GL.iNet Brume 2
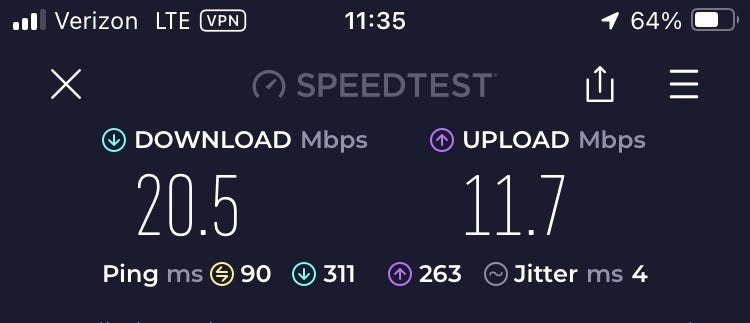
Connected to Tailscale exit node and DERP relay server on Raspberry Pi 4B
- Verizon LTE connection used on iPhone SE 3rd gen. I live in a rural area so the variance in traffic on this tower’s antenna is going to be fairly minimal. Still uncontrolled and using Ookla instead of iperf.
- Also note that I am running my own DERP relay server on the same Raspberry Pi which my exit node is hosted on. No public relay server was used. This is a bit complex to setup and documentation is minimal. I used this guide.
- GL.iNet Brume 2 (Wireguard) plugged into LAN 2 of Xfinity router and Pi 4B (Tailscale exit node/DERP relay) plugged into LAN 1.
- Server location is ~7 miles down the road
Server location internet speeds *without* any VPN: ~800 Mbps down, ~24 Mbps up
So, as you can see the download speed clearly does not exceed 24 Mbps due to the upload speed limitation of the server location’s internet. Still, the similarity in speeds between bare Wireguard and Tailscale with self hosted relay server is impressive! Without the self-hosted Tailscale DERP relay server though, I would probably be routed through Tailscale’s public NYC server and my speeds would have suffered immensely.
Which one is right for me?
If you do not have CGNAT at the location you will host your VPN server, then Wireguard is undoubtedly the best option to go with. To know if your ISP uses CGNAT, you can either call them and ask or check to see if you are able to port forward from your router on your own. With CGNAT, you would have to call your ISP to request port forwarding to which they may respond “no”. To check if your home network is behind CGNAT, follow the instructions here: https://icanhazvpn.com
If you do have CGNAT (double NAT) at your server location, then Tailscale, AstroWarp, or ZeroTier are your only options. Tailscale/ZeroTier/AstroWarp are also better options for those who are maybe more uncomfortable with networking (ex. port forwarding).
Whichever you choose, using a GL.iNet router reduces the complexity significantly. These routers have both, Wireguard and Tailscale, built into their router devices. However, the built-in Tailscale application is only meant to be used as a client (additionally it is only in beta), though you CAN manually enable the exit node to use it as a server.
Lastly, there is no reason why you can’t use both! Redundancy is always a good thing. I personally use Wireguard for my primary VPN and my Tailscale exit node + self-hosted DERP relay server is my backup in case my Wireguard router goes down for any reason. My 3rd backup is another Tailscale exit node at an entirely different location, though it has much slower speeds due to being a Mi-Fi device connection.
To give it a go yourself, check out the VPN Guide page.
And for a custom DERP relay server to ensure your speeds are not slowed down, see my new Diamond Tier (for Nomads).
Thanks for reading!